Table of contents
You can now use Checkly to monitor API endpoints secured with TLS Client Certificates. This post dives into why and how you would use client certificates and mTLS (Mutual TLS) in your API infrastructure. Let's go!
mTLS and Client Certificates primer
We'll keep this short as there are many great blog posts out there explaining mTLS (Mutual TLS) in great detail. But here is the gist:
- mTLS is used to authenticate clients, whereas "normal" TLS just authenticates the server. The authentication is now mutual!
- mTLS works using public key cryptography. This means there is a public key —also commonly referred to as the "certificate" — and a private key. Together we refer to them as the client certificates.
- mTLS can be used on any TCP or HTTP connection. It depends on the specific implementation of your web server, router, API gateway or service mesh. Examples here are Nginx, Kong and Linkerd.
- mTLS is one of the puzzle pieces of building a Zero Trust Network as it strictly controls which clients are allowed to connect to a service regardless of where a user or device is connecting from (VPN, internal network etc.) and regardless of further user credentials.
Using Checkly to monitor mTLS endpoints
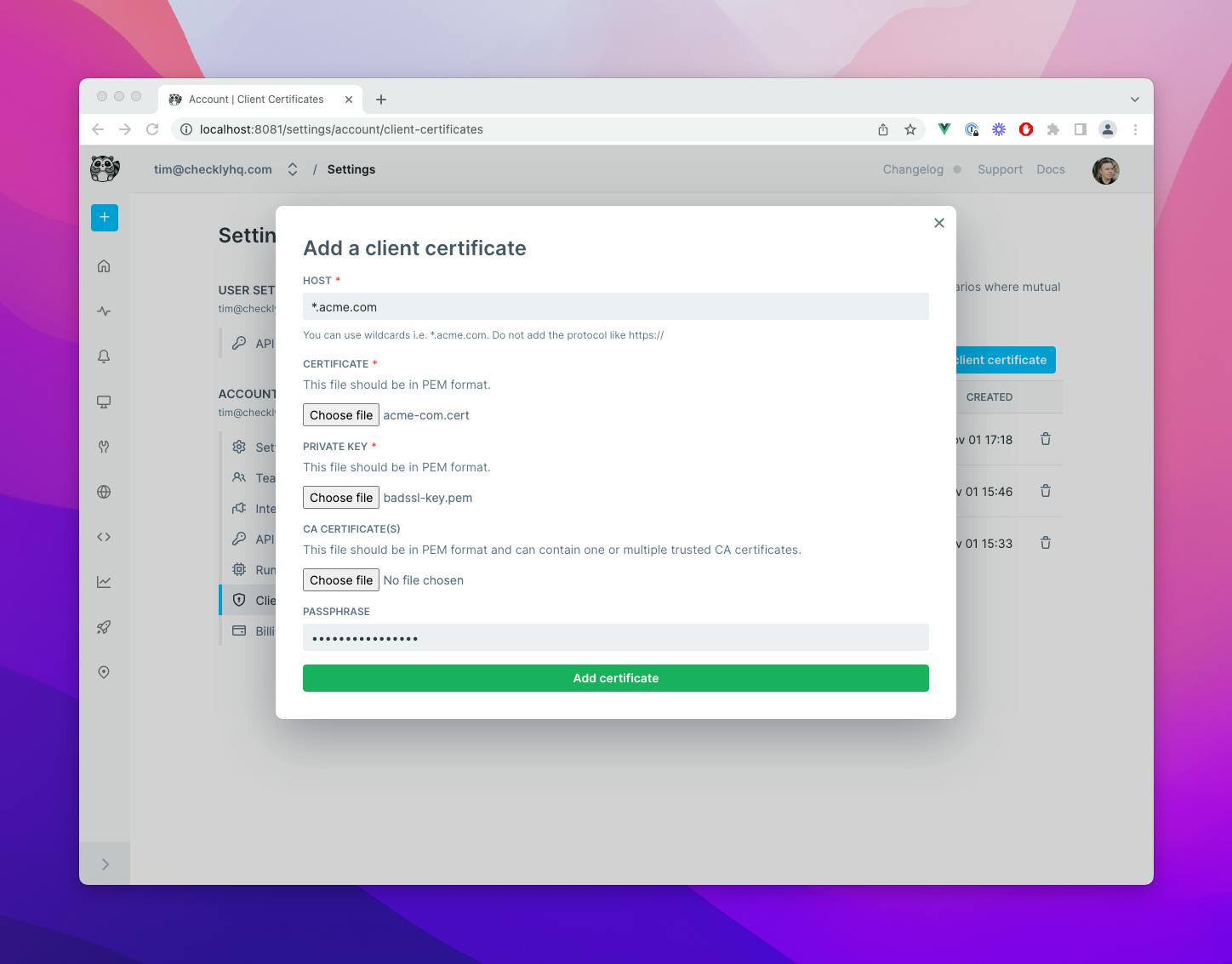
Setting up API monitoring for your mTLS authenticated API endpoints is extremely easy. Just provide the following ingredients:
- Domain / hostname. We support wildcards like
*.acme.com. - Certificate & private key.
- Optionally a password and CA certificate.
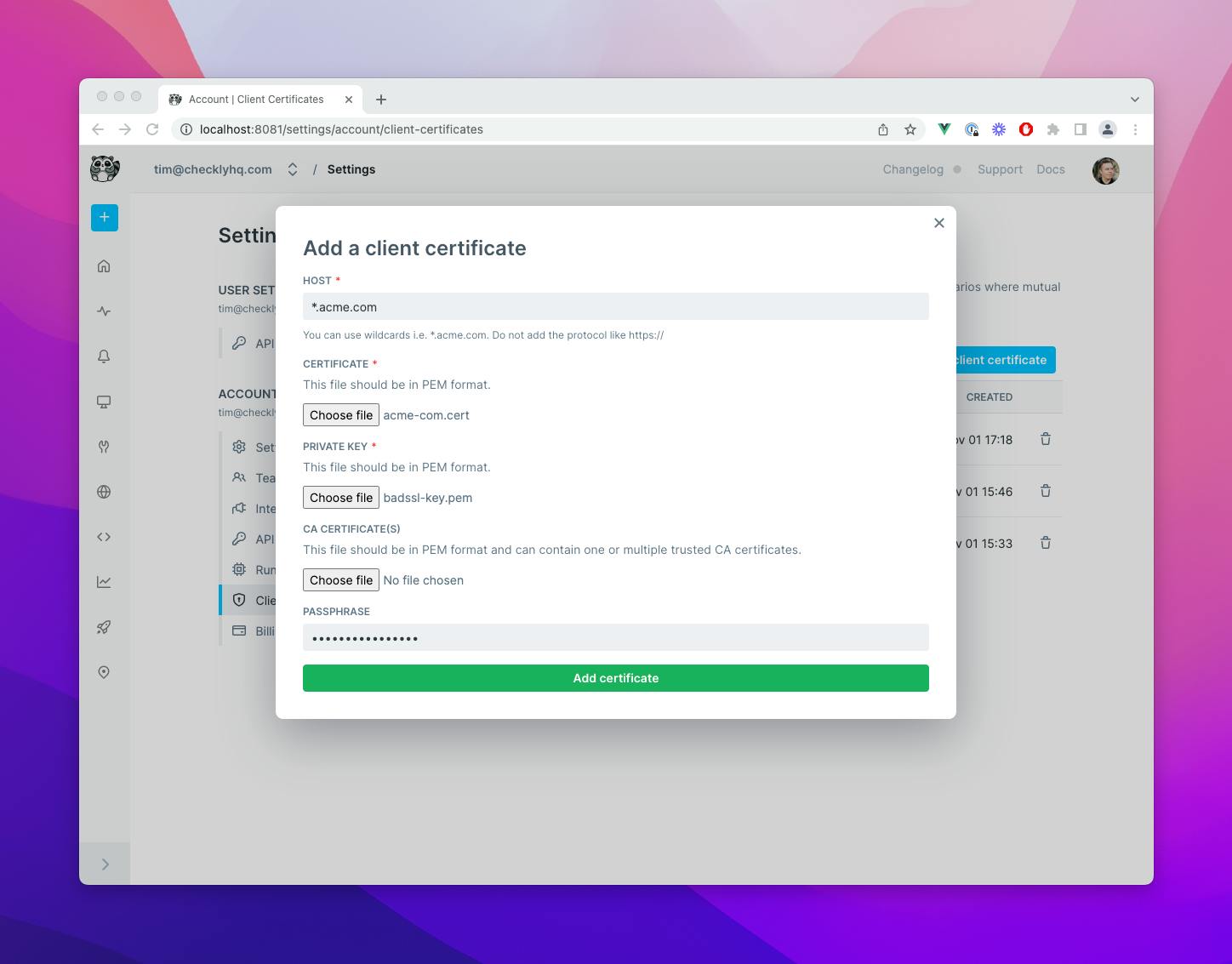
You can configure that in our web UI or use our public API. Make sure your certificates and private key are in PEM format. Note that support for Terraform and Pulumi is coming soon.
If you have them in PKCS12 format, just convert them with the following incantation of the openssl command 👇
openssl pkcs12 -in <CERT>.p12 -out <PRIVATE_KEY>.key -nodes -nocerts
openssl pkcs12 -in <CERT>.p12 -out <CERTIFICATE>.cert -nokeysuse openssl to convert a PKCS12 bundle to PEM format
After adding the certificate, any API checks that target this host, i.e. https://api.acme.com will be instrumented with the client certificate. Or, in other words, there is no need to add the client certificate to all relevant API checks. Checkly does the matching for you.
And that is it! Client Certificates are now available to all Checkly users on an Enterprise plan.
Further reading
Read more on how to use client certificates in our docs and check out our public API documentation on how to manage client certificates programmatically.